ON Risk Monitoring
By Taelor Sutherland, Associate Editor
Every organization needs a way to monitor any risks that may come their way. Security magazine has highlighted a few recently released risk management products.
CyberSaint
Manage All Risks in One Platform
CyberStrong is purpose-built for enterprise cyber risk management. Users can manage cybersecurity with a standards-based, risk-centric lens through which can illustrate a program's impact. Users can identify and quantify cyber risks quickly, prioritizing controls using financial metrics through models such as the FAIR model or NIST 800-30. Image courtesy of CyberSaint
Find out more at cybersaint.io

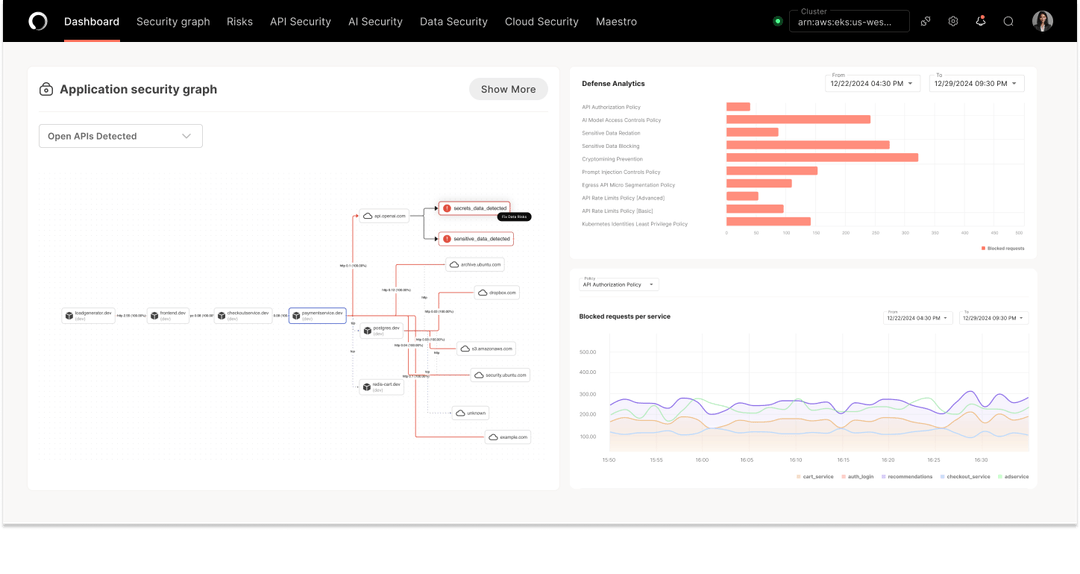
Operant AI
Uses AI to Manage Access Control
Operant AI announced AI Gatekeeper, a new product that brings end-to-end runtime AI protection to everywhere enterprises are deploying AI Applications and AI Agents – from Kubernetes to hybrid and private clouds. AI Gatekeeper not only brings Operant’s 3D Defense capabilities beyond Kubernetes, it also provides defenses against rogue agents, including trust scores, agentic access controls, and threat blocking for MCPs (Model Context Protocols) and Agentic AI Non-Human Identities (NHIs). Image courtesy of Operant AI
Find out more at www.operant.ai
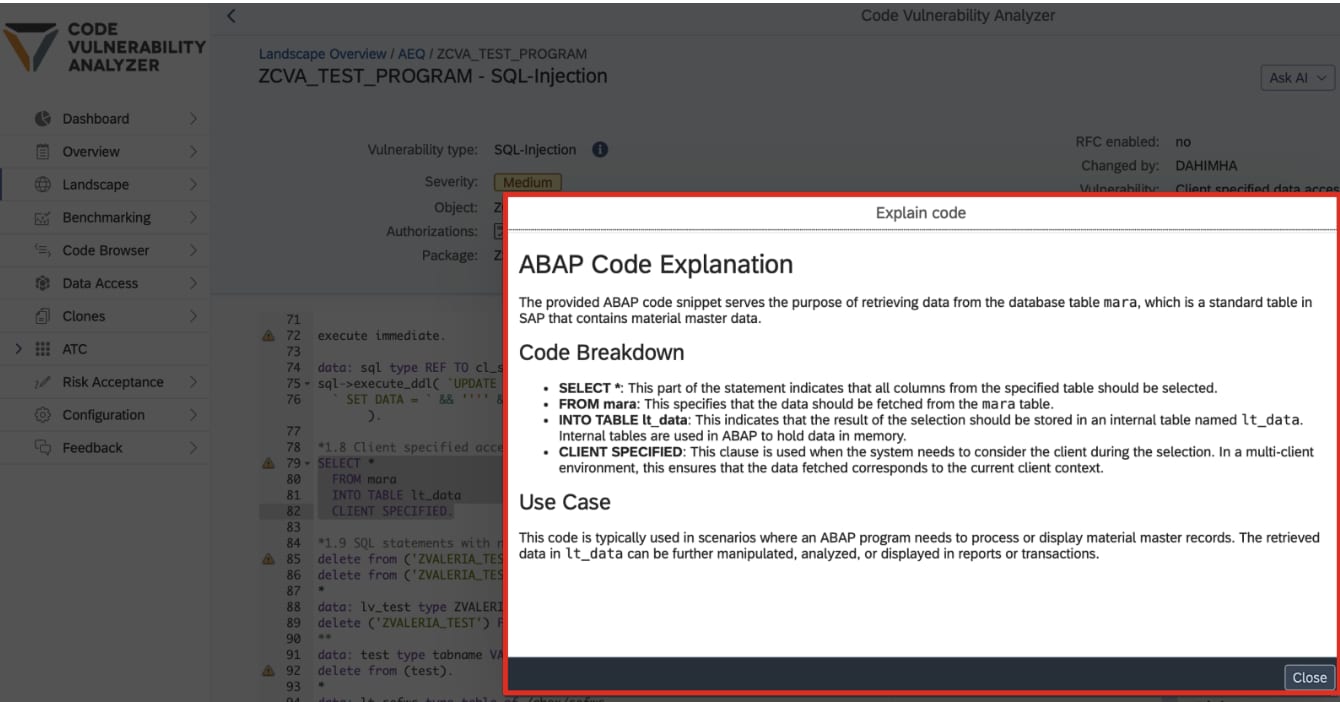
SecurityBridge
Detects Malicious or Vulnerable Code
With the release of SecurityBridge Platform V6.31, SecurityBridge is introducing a set of AI-powered functions for early adopters within the SecurityBridge Code Vulnerability Analyzer (CVA) app. These features aim to help customers better understand vulnerabilities in custom ABAP code and clarify the purpose of specific code snippets within their systems. This built-in feature simplifies the understanding of ABAP code by explaining the purpose and functionality of a selected code snippet. It is particularly valuable for users unfamiliar with ABAP’s complexities but who want to comprehend the behavior of specific code. Image courtesy of SecurityBridge
Find out more at securitybridge.com
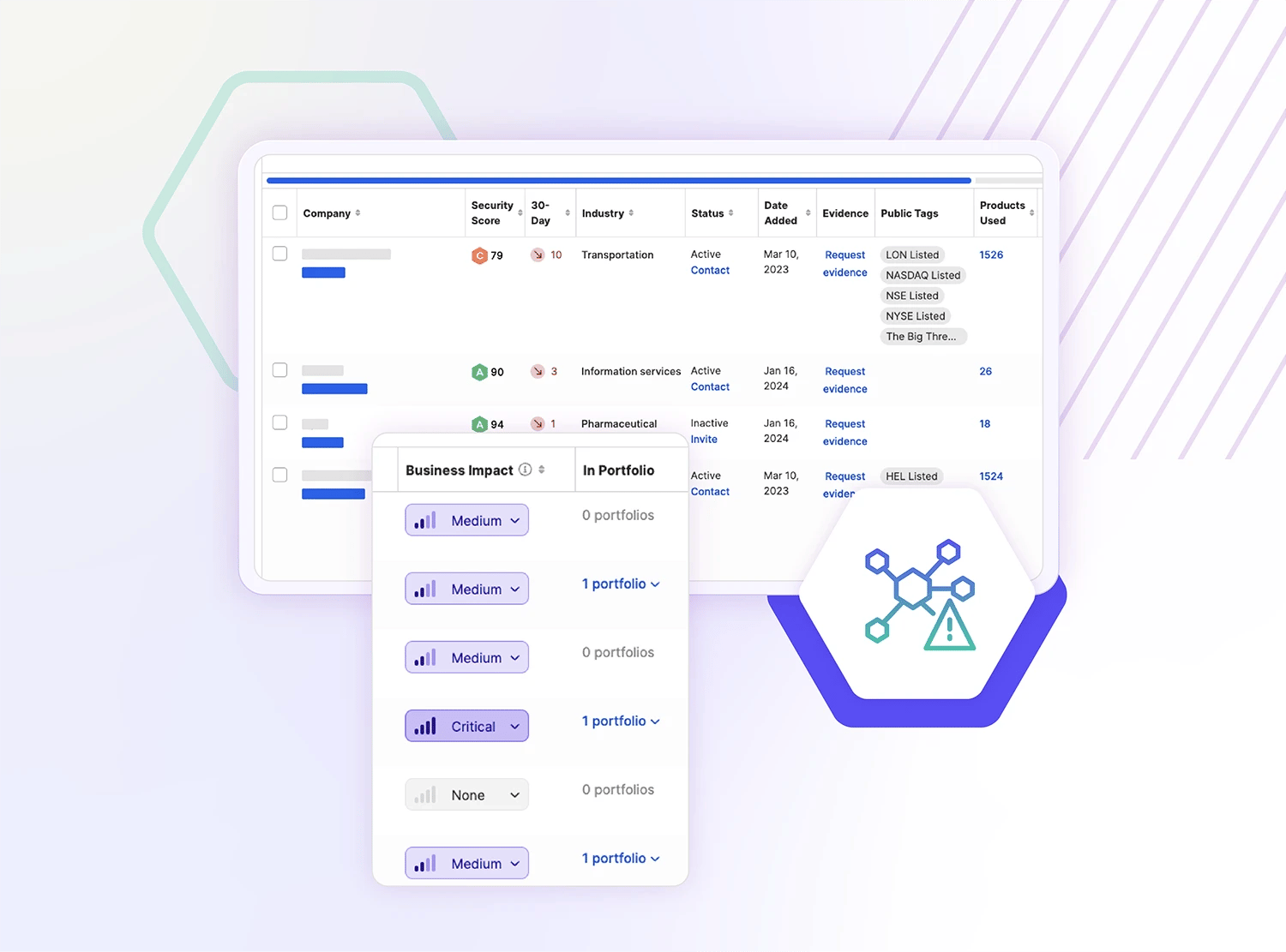
SecurityScorecard
Manage Third Parties To Reduce Risk
Users can streamline collaboration with internal stakeholders and their third-parties in one dashboard, and create plans for your vendors to improve their security posture. Users can also generate dynamic remediation plans and prioritize critical vulnerabilities and assign individuals to fix issues. Users can see progress in real time, saving hours and reducing ecosystem risk. Continuously monitor and assess your third-parties with breach and incident data to ensure compliance and safeguard your supply chain against potential cyber threats. Image courtesy of SecurityScorecard
Find out more at securityscorecard.com
TrackVia
Automatically Flags Safety Concerns
TrackVia simplifies the process of conducting safety checks and inspections. Ucan standardize safety protocols across all locations, perform thorough inspections using mobile devices and capture data and photos directly from the field. TrackVia provides tools to automatically flag safety issues during inspections, assign corrective actions to responsible team members and track issue resolution in real time. Image courtesy of TrackVia
Find out more at trackvia.com